User:ConsciousCode/sandbox: Difference between revisions
No edit summary |
(Homework) |
||
| Line 1: | Line 1: | ||
{{quote|Physical access is root access|Security Operations}} | |||
Hardware hacking means modifying existing electronics to use them in a way they were not intended to be used. Normally this means hacking in order to gain privilege escalation and compromise security, but it's equally applicable to unlocking the hidden capabilities of a DVD player to act as a file server for backups. | |||
The complexity of a hack depends primarily on the intended market of the device. Usually the cheaper and simpler something is, the less they bothered to remove extra debug and programming hardware before sending it to market. Smartphones have an extreme level of complexity so they tend to be heavily locked down and require a lot of research, if it's even possible for a hobbyist. On the other hand, devices which don't have any significant level of miniaturization tend to still have everything the developers used to create the hardware in the first place. | |||
== Audience == | |||
This how-to is intended for anyone with a passing knowledge of circuitry, but not much else. If you know what "Arduino" is, this is probably for you. It can get slightly technical, but even absolute beginners should be able to follow along with Google open to look up anything they're not familiar with. | |||
=== Scope === | |||
This article is specifically focused on techniques to start unlocking hardware capabilities. Soldering, using the tools, and firmware are all out of scope and will require additional research by the reader. The topic itself is already incredibly broad, so it doesn't make sense to talk about the specific techniques after initial hacking. Soldering is an art form in itself, one which requires a lot of practice to get good at, and firmware varies so wildly between chips that it would take a dozen more articles of this length to even give an overview. Above all else, this article is to introduce people to the basics of hardware hacking and to encourage more research to actually put these techniques to practice. | |||
== Terminology == | == Terminology == | ||
; Ground | ; GND (Ground) | ||
: A reference to 0 voltage which determines the voltage of the rest of the circuit. | : A reference to 0 voltage which determines the voltage of the rest of the circuit. | ||
; Vcc | ; Vcc | ||
| Line 20: | Line 26: | ||
; Full-duplex | ; Full-duplex | ||
: A two-wire bidirectional bus where each line transmits in only one direction, so data can be flowing in both directions simultaneously. | : A two-wire bidirectional bus where each line transmits in only one direction, so data can be flowing in both directions simultaneously. | ||
; Serial / Parallel | ; Serial / Parallel | ||
: A line which communicates one bit at a time, rather than a parallel line where eg 8 bits of a byte are sent across 8 wires simultaneously. | : A line which communicates one bit at a time, rather than a parallel line where eg 8 bits of a byte are sent across 8 wires simultaneously. | ||
; Synchronous / Asynchronous | ; Synchronous / Asynchronous | ||
: A bus | : A synchronous bus has a clock which synchronizes a line between a controller and peripheral. | ||
; Active high / low | |||
; Active high/low | |||
: The line is considered "on" or the 1 bit when the voltage is high/low. Active low sounds weird, but it's primarily used for alert signals because it can be implemented with a single transistor. | : The line is considered "on" or the 1 bit when the voltage is high/low. Active low sounds weird, but it's primarily used for alert signals because it can be implemented with a single transistor. | ||
; Interrupt | ; Interrupt | ||
| Line 38: | Line 38: | ||
; PCB | ; PCB | ||
: Printed Circuit Board | : Printed Circuit Board | ||
; Bodge wire | |||
: A wire added to a circuit board by an end-user to connect things that weren't connected before. | |||
== Tools == | == Tools == | ||
Most of | When ordering tools, you can find them on Amazon and they'll arrive in days while they're 2-3 times cheaper on AliExpress but take a month to ship from China. | ||
=== Disassembly === | |||
Most of these you probably already have or some equivalent. They're used to disassemble a device to expose them for hardware hacking. | |||
* '''Screwdrivers''' | |||
** Usually only phillips are needed of various sizes. A hex driver set is a valuable tool for taking anything apart. | |||
* '''Spudger''' | |||
** This is any thin, flat object which can be used to pry a tabbed case apart. Ideally this should be plastic or rubber because there's less chance of it damaging the casing or cutting your fingers when you slip. | |||
* '''Superglue''' | |||
** For when you inevitably break the case, superglue can help repair it. | |||
=== Investigation === | |||
These tools are used for investigating a circuit when signals are mislabeled or not labeled at all. None are actually required, but they make life easier. | |||
* '''Multimeter''' ($10 Amazon, $5 Ali) | |||
** Voltmeters can identify power supplies, voltage levels, and active signals. | |||
** Continuity testers help identify where wires are connected. | |||
** Ohmeters determine resistances, which can be used in Ohm's Law calculations. | |||
* '''Single-Board Computers''' with these interfaces exposed | |||
** Raspberry Pi Zero ($10) | |||
* '''Multi-interface adapters''' (if you can't get an SBC) | |||
** FT232H USB to JTAG/UART/I2C/SPI Module ($18 on Amazon, $6 on AliExpress) | |||
** CH341A USB to UART/I2C/SPI ($9 on Amazon, $4 on Ali) | |||
* '''Logic Analyzer''' ($13 Amazon, $5 on Ali) | |||
** These are not necessary, but can be invaluable for identifying unmarked headers. | |||
* '''Oscilloscope''' ($30 Amazon, $25 on Ali) | |||
** Useful for debugging faulty and analog signals. Good oscilloscopes run several hundred dollars, but functional versions can be found for $25. | |||
Single-interface adapters (especially for UART and i2c) are available, but not much cheaper than the multi-interface adapters. | Single-interface adapters (especially for UART and i2c) are available, but not much cheaper than the multi-interface adapters. | ||
=== Soldering === | |||
'''Soldering''' is melting a low melting-point metal called "solder" to connect components to a circuit board. It's not always necessary in hacking, but can be incredibly useful to attach wires so they don't have to be held in place. | |||
* '''Solder''' ($5) | |||
* '''Soldering iron''' ($10) | |||
* '''Solder flux''' ($5 Amazon, $2 Ali) | |||
* '''Fume extractor/fan''' (varies) | |||
** Not strictly necessary, you can solder in a well-ventilated area but even then these are a good idea to have because breathing in heavy metals isn't usually a good idea. | |||
* '''Solder wick braid''' ($4 Amazon, $2 Ali) | |||
** Used to remove excess solder and remove soldered components | |||
* '''Heat gun''' ($12 Amazon, $5 Ali) | |||
** Relatively rare you need to use one, mostly useful for adding or removing components with a lot of pins, or when there's massive heatsinks a soldering iron can't heat up fast enough. | |||
=== Other === | |||
* '''SOIC8 programmer test clip''' ($8 on Amazon, $2 on Ali) | |||
** Useful for more advanced hacking when you can find an external program memory, allowing you to read and write firmware without removing it. | |||
== How-to == | |||
=== Selection === | |||
When hardware hacking, the kind of device you try to hack is very important. You want cheap, old, low-effort devices ideally owned by millions of people. If you don't have one in mind, thrift stores are an excellent source of these. Always keep in mind the capabilities of the device; you will never be able to turn a DVD player into a high performance computer, but you might be able to embed other devices into it to make it a multimedia center. | |||
Unfortunately many devices with high hack-potential are also incredibly tightly locked and not even professional hackers have managed to get them to do anything except their intended function. This includes most smart phones, which are just too tightly engineered to have easy access points, but also products like Amazon Alexa have been found to be near unhackable, as cool as it would be to install your own custom assistant firmware. | |||
=== Google it === | |||
As fun as it can be to figure out how to hack a device, there's a good chance someone else has already figured it out and they probably did it better than you can. Google the model number before you even open it, because you might find someone else determined it to be too much trouble to hack and you can save the effort. | |||
=== Open the case === | |||
Before anything, unplug the device and maybe even let it rest 30 minutes. | |||
Great care must be taken when opening any device, especially new ones, because the case may have hidden tabs you can accidentally break off or glue which requires enough force to break the case. It's usually possible to open a device without any damage or force. Look for screws, which may be under stickers or rubber feet, and stick flat objects into any grooves you see. Apply some force to see if it will give, but if you have to use too much you probably missed a fastener somewhere. | |||
At each step of the disassembly, take a picture of what it looked like so you know what it should look like after you put it back together. Take note of the size and shape of each screw as well, as they may differ and require some kind of organization to match them back to their original place. You don't have to be so thorough as to match each screw to exactly where it came from, just which sizes go with which locations. | |||
=== Disassembly === | |||
Once the case is open, you'll see the guts of the device itself. This is the easy part of disassembly because at this point it's designed for serviceability. Keep taking pictures and unscrew every circuit board or component you can find until everything is in pieces. This lets you see all sides of the boards, any markings they might have, and any headers they might be hiding. Often devices will contain multiple boards connected by board-to-board cables like flat cables or JST connectors. You need to unplug them as needed, also taking note of how and where they connect to each other. | |||
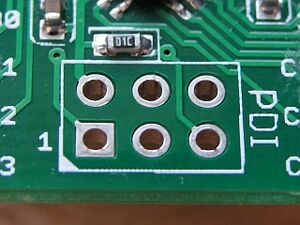
[[File:Pdi_bmp001x4_320.jpeg|thumb|right|An unpopulated header labeled "PDI" (Programming and Debug Interface). By convention, the square pin denotes pin 1 and ground. Image Credit: [http://www.batsocks.co.uk/readme/pdi_headers.htm Batsocks]]] | |||
If you see a thick board with a lot of black tubes on it, this is probably the power supply unit and you should be very careful when handling it. They aren't dangerous on their own, but those big black tubes are called "capacitors". They're discrete components which store charge like batteries, but are optimized to release all their energy at once. Unscrew the PSU, then take your screw driver and touch the metal bits underneath the black tubes to discharge them. If they're thumb-sized or bigger, they may make a loud POP, and afterwards do nothing. Unless they're in a CRT TV they're probably not lethal, but it will hurt a lot if you touch them before discharging. Most products made after the 1990s will only have these massive capacitors on the PSU, and if they do have them on other boards they're probably there for their high capacitance (to eg filter audio signals) rather than their charge capacity. | |||
=== Header Hunting === | |||
The first things you should look for are headers. These stand out a ''lot''. They're lots of big holes close together and covered in metal. Usually during development, these have header pins soldered into them so the developers can easily plug in their test equipment. Then when they go to market, they aren't removed because doing so would mess up circuit routing, require they be added back in if further revisions are done, and then there'd be no way to test hardware faults reported by customers. Because they're used for testing and development, they tend to give a lot of access to the hardware for little to no effort, though sometimes ICs are programmed to disable their debug capabilities. Rarely they'll even still have pins in them (to make flashing the firmware at the factory easier). | |||
[[File:Debug-tag-connect-footprint.jpg|thumb|right|A 6-pin Tag Connect interface. Tag Connect is a proprietary connection standard which I have yet to see in the wild, but if you do find one you can guarantee it's used for debug and ICSP. Image Credit: [https://partsbox.com/blog/choosing-a-debug-programming-connector-2019.html PartsBox]]] | |||
Once found, look for [[#silkscreen|silkscreen]] text nearby which labels the pins. There's a lot of variation in the labels, but generally it should make at least some sense. Any which are labeled ICP, ISP, ICSP, PDI, Debug, Comm, Port, etc are probably going to be very useful. | |||
=== Test Pads === | |||
[[File:GGXAK.jpg|thumb|right|A bunch of unlabeled test pads. When they're close together like this, there's a good chance they're meant for pogo pin rigs and may have been used to program firmware in the factory. Image Credit: [https://electronics.stackexchange.com/questions/437423/what-are-these-round-pads-on-the-bottom-of-a-pcb StackOverflow]]] | |||
If no interesting headers can be found, you can also look for test pads. These are moderately-sized (around 1 mm) circles or squares of (possibly tinned) exposed copper which give easy access to a line. In generous designs, they'll even be labeled, but this is less common than for headers. | |||
If the test pads aren't labeled, it's time to do research and use your continuity tester to cross-reference with IC datasheets. This can be tedious but rewarding for what it can uncover. Often, test pads expose unused pins on an IC, which can be incredibly useful for custom firmware. | |||
=== Research === | |||
More often than not, headers and test pads either don't exist or aren't properly labeled. When this happens, it's time to Google the IC part numbers. This is probably the most frustrating step, as manufacturers treat their datasheets as confidential. They like to hide them behind inquiry forms, and you can bet your inquiry is going straight into the trash if you're ''ordering'' less than 1000 units, much less inquiring about a unit they've already sold. Luckily they don't seem to be especially litigious for sites which host datasheets very clearly watermarked as confidential, so they still tend to get out. | |||
First, try googling just the part number. It might not be confidential, or it might be consumer-grade so they actually ''want'' you to see it. It might be on the manufacturer's website, a distributor, a datasheet aggregator, or just a raw PDF. It's always nice when this is all you need to find it. | |||
Otherwise, you can try searching "<part number> datasheet" or even "<part number> datasheet ext:pdf". Sometimes even this isn't enough, and you have to branch out. You can try searching for "<part number> pinout"; it's not ideal, since you won't know exactly how the chip works, but a pinout can at least give you an idea of what's going on. Occasionally I've found pinout images or EDA footprints created by hobbyists who found it somehow. Datasheet aggregators like [https://alldatasheet.com alldatasheet.com] list ICs with similar part numbers and their descriptions, and oftentimes manufacturers won't significantly change the pinouts between versions. When using this information, you should always double check to avoid frying a chip. | |||
In the worst case scenario where no information about a chip can be found, pinouts may need to be reverse-engineered. Power pins are the easiest because they can be found with multimeters and visual clues like the width of the wire. Ground will always be made of big blobs of copper that fill unused areas, while Vcc tends to have slightly larger wires. Circuits almost always have more than one chip, so if information can be found on them they can be cross-referenced along with labeled test pads and connectors. Buses tend to be routed together, so through visual inspection groups of 2-5 wires can be identified and connected to a logic analyzer. If there are no test pads on these and you're really desperate, you can carefully scrape off the solder mask to expose the bare copper underneath. If you accidentally cut the wire, you can solder a bodge wire on top without much issues. | |||
The easiest way to match other pins, headers, and pads to an IC's pins is to put one of the continuity tester's probes on the known signal, and drag the other probe across each row of pins until it beeps. This gives you a general idea of where it's connected which can be narrowed down until the exact pin is found. | |||
Sometimes you'll find an 8-pin EEPROM memory chip nearby. These are great because they usually store firmware or configuration data. Then if you can't find datasheets, you can still dump the firmware, detect what architecture it's using, and convert it to human-readable code it to see what it's doing. | |||
[[File:EeENZ.jpg|thumb|right|Glob tops themselves can't be hacked, though this doesn't preclude hacking the rest of the circuit with the glob type acting as a black box. Image Credit: [https://electronics.stackexchange.com/questions/9137/what-kind-of-components-are-black-blobs-on-a-pcb StackExchange]]] | |||
Don't be afraid to give up on a chip, either. If no information can be found, it's not really worth reverse-engineering because even if you reverse engineer everything you probably won't be able to hack it. In cheaper products, there are even what are called "[https://en.wikipedia.org/wiki/Electronic_packaging*Glob-top glob-tops]" which are bare silicon dies coated in black epoxy which are never labeled. | |||
=== Hacked === | |||
Once you have a decent understanding of the circuit and how it functions, you should have a good idea of how it can be changed and what to do to change it, or at the very least a lead on how to research it. The easiest hacks are those that require only a simple rewiring, or replacing switches with relays to automatically push buttons etc. The most rewarding hacks will involve rewriting firmware or embedding an extra microcontroller (with its own firmware) to control peripherals as needed. | |||
Sometimes you'll find a circuit can't really be hacked with your skill level, or what's available isn't that interesting. For these cases, it's best to cut your losses and either give it back to Goodwill or strip it for parts to use in other projects. Connectors, buttons, switches, LEDs, batteries, and even some daughterboards like the PSU are all useful. Occasionally they'll have a well-documented IC which is worth harvesting as well. Don't bother harvesting discrete components like resistors, capacitors, or inductors unless you're severely strapped for cash, they cost less than $5 for packs of 500. | |||
== Silkscreen == | |||
Most PCBs have what's called a "silkscreen", which is white or black ink drawn on the board to aid manufacturing and keep track of which components go where. Most of these will be "reference designators", an alphabetic prefix with a numerical suffix. This isn't super useful, but can aid in identifying what signals various wires carry. Some common reference designators include: | |||
* '''R''' - Resistor, restricts the flow of voltage | |||
* '''C''' - Capacitor, stores charge to suppress voltage ripples and filter signal frequencies | |||
* '''L''' - Inductor, resists high frequencies | |||
* '''D''' - Diode, only lets current flow in one direction | |||
* '''Q''' - Transistor, a kind of electronic switch | |||
* '''U''' - Integrated Circuit | |||
* '''F''' - Fuse, literally breaks if too much current flows through it to protect from power surges | |||
* '''H''' - Hardware eg screws | |||
* '''J''' - Jack, some kind of connector to carry signals into or off of a PCB | |||
* '''JP''' - Jumper, exposed copper pads close together which lets you connect two lines together, usually to set some semi-permanent configuration by the manufacturer | |||
* '''S''' - Switch or button | |||
* '''T''' - Transformer, usually used in power supplies to convert AC to DC | |||
* '''TP''' - Test Point, exposed copper pads which give easy access to a signal line or power wires | |||
* '''X(TAL)''' - Crystal oscillator | |||
* '''H''' - Pin Header | |||
There are hundreds more, and they aren't always what they normally mean. Reference designators are not a standard, they're maintained by convention alone. | |||
The ones you want to pay the most attention to are U, H, J, and JP (IC, Header, Jack, and Jumper) although it's also usually obvious what they are just by looking at them. | |||
== Interfaces == | == Interfaces == | ||
There are 5 interfaces which you'll find most often in hardware hacking: RS-232 (aka UART), SPI, i2c, JTAG, and SWD. More recognizable interfaces like USB are primarily used for inter-device communication, though embedded USB does exist. There are other more exotic interfaces like 1-wire, UNIO/O, CAN, i2s, CEC, and a veritable zoo of debug interfaces, but they aren't very common or useful for hacking. | |||
=== RS-232 === | === RS-232 === | ||
'''RS-232''' (Recommended Standard 232) is an extremely old serial protocol from 1960 used for teletypewriter operator consoles and more rarely inter-chip communication. Nowadays it's more commonly referred to as '''U(S)ART''' (Universal Synchronous/Asynchronous Receiver/Transmitter) which is technically a | '''RS-232''' (Recommended Standard 232) is an extremely old serial protocol from 1960 used for teletypewriter operator consoles and more rarely inter-chip communication. Nowadays it's more commonly referred to as '''U(S)ART''' (Universal Synchronous/Asynchronous Receiver/Transmitter) which is technically a physical implementation used for communication standards such as RS-232. Because UART isn't a communication standard per-se, it has a lot of variation in its interface. | ||
At its most extreme, a UART-based interface can be a single wire half-duplex interface, where the peripheral and controller both have control over the bus and have to agree | At its most extreme, a UART-based interface can be a single wire half-duplex interface, where the peripheral and controller both have control over the bus and have to agree ahead of time which one should control the bus at any given time to avoid thrashing communication. | ||
Usually a chip's UART will use two wires (Tx and Rx) to implement a full-duplex stripped down RS-232. | Usually a chip's UART will use two wires (Tx and Rx) to implement a full-duplex stripped down RS-232. UART is almost always signaled with 0V for bit 0 and 3.3V for bit 1. Sometimes there is also frame bits to let devices know when communication starts, checksum bits to detect transmission errors, or exotic word sizes, all things which should be checked for if the defaults don't work. Baud rate (the frequency the bits are transferred) will also probably need adjusting because there's a lot of variation. 9600 and 115200 are the most common I've seen (in bits per second). | ||
More rarely a chip will implement more RS-232 signals which you can connect to most USB adapters. They're almost never necessary because they communicate readiness to receive data, and even the cheapest microcontrollers are fast enough to always be available. If you ever need them, it's good to know that RS-232 calls the terminal that connects to a device "DTE" (Data Terminal Equipment) and the device itself "DCE" (Data Communications Equipment). This was from the dawn of computers when you had one big shared mainframe and dozens of "dumb terminals" which let you run commands and see their results. | More rarely a chip will implement more RS-232 signals which you can connect to most USB adapters. They're almost never necessary because they communicate readiness to receive data, and even the cheapest microcontrollers are fast enough to always be available. If you ever need them, it's good to know that RS-232 calls the terminal that connects to a device "DTE" (Data Terminal Equipment) and the device itself "DCE" (Data Communications Equipment). This was from the dawn of computers when you had one big shared mainframe and dozens of "dumb terminals" which let you run commands and see their results. | ||
| Line 67: | Line 185: | ||
In 2022, the OSHWA (Open Source HardWare Association) changed the acronyms used by SPI because of their tacit usage of slavery terminology. For at least a few more years one is likely to see both kinds in the wild, so both are listed here. | In 2022, the OSHWA (Open Source HardWare Association) changed the acronyms used by SPI because of their tacit usage of slavery terminology. For at least a few more years one is likely to see both kinds in the wild, so both are listed here. | ||
* '''MISO''' / '''POCI''' - Master In Slave Out / Peripheral Out Controller In | |||
* '''MOSI''' / '''PICO''' - Master Out Slave In / Peripheral In Controller Out | |||
* '''SS''' / '''CS''' - Slave Select / Chip Select, active-low enabling a chip to listen. Sometimes omitted if only one device is on the bus | |||
* '''SDI''' / '''SDO''' - Serial Data In / Serial Data Out, can be either POCI or PICO depending on if the device is a controller or peripheral | |||
* '''INT''' - Interrupt, relatively rare for SPI | |||
SPI can be half-duplex using only one wire (plus Chip Select), but this is very rare. Communication is initiated by the controller, then it stays quiet while it waits for the peripheral's response. | SPI can be half-duplex using only one wire (plus Chip Select), but this is very rare. Communication is initiated by the controller, then it stays quiet while it waits for the peripheral's response which has some method of saying when it's done. | ||
Variations exist for transmitting 2 (Dual SPI), 4 (Quad SPI or QSPI), and even 8 (OctoSPI) bits at a time. QSPI is actually used by most modern SD cards. For low-level hacking, only Single SPI is actually useful because the others are meant for high-bandwidth memory rather than eg program memory. | |||
=== i2c === | === i2c === | ||
'''i2c''' (Inter-Integrated Chip) is an old (1980s) communication protocol which is used nowadays for peripheral control. Unlike SPI, it's packetized and toggled by 7 or 10 bit addresses. It's very useful for controlling peripherals directly when you can't get access to the microcontrollers. | '''i2c''' (Inter-Integrated Chip) is an old (1980s) communication protocol which is used nowadays for peripheral control. Unlike SPI, it's packetized and toggled by 7 or 10 bit addresses. It's very useful for controlling peripherals directly when you can't get access to the microcontrollers. | ||
* '''SDA''' - Serial DAta | |||
* '''SCL''' - Serial CLock | |||
* '''INT''' - INTerrupt, very common for i2c | |||
=== JTAG === | === JTAG === | ||
'''JTAG''' (Joint Test Action Group) is an old (1980s) synchronous factory test standard allowing boundary scanning and ICSP of daisy-chained chips. It uses no less than 5 signals, and often many more, but is very powerful if you can find it because it usually gives you complete and total access to every JTAG-enabled chip on the board. | '''JTAG''' (Joint Test Action Group) is an old (1980s) synchronous factory test standard allowing boundary scanning and ICSP of daisy-chained chips. It uses no less than 5 signals, and often many more, but is very powerful if you can find it because it usually gives you complete and total access to every JTAG-enabled chip on the board. | ||
* | * '''TDI''' - Test Data In | ||
* | * '''TDO''' - Test Data Out | ||
* | * '''TCK''' - Test ClocK | ||
* | * '''TMS''' - Test Mode Select | ||
* | * '''TRST''' - Test ReSeT (optional) | ||
=== SWD === | === SWD === | ||
'''SWD''' (Serial Wire Debug) is a very new (2017) 2-wire variant of JTAG defined used by low pin count ICs. Unlike JTAG, it does not support daisy chaining and so the access it provides is limited to a single IC and interfaces which can be explicitly accessed via the JTAG registers. If you find an unlocked SWD interface, you're done. It gives you complete control over the system with only 2 wires, and is powerful enough to let you read ''and'' write registers and memory of the microcontroller while it's running. | '''SWD''' (Serial Wire Debug) is a very new (2017) 2-wire variant of JTAG defined used by low pin count ICs. Unlike JTAG, it does not support daisy chaining and so the access it provides is limited to a single IC and interfaces which can be explicitly accessed via the JTAG registers. If you find an unlocked SWD interface, you're done. It gives you complete control over the system with only 2 wires, and is powerful enough to let you read ''and'' write registers and memory of the microcontroller while it's running. | ||
* | * '''SWDIO''' - Serial Wire Data Input/Output | ||
* | * '''SWCLK''' - Serial Wire CLocK | ||
=== | == Examples == | ||
=== Laptop Webcam === | |||
{{gallery | |||
|File:PXL 20230220 003850486.jpg | |||
| A Sony CN0319-S33B-0V02 module. It's properly colored, so very straightforward to convert. It does have two USB pairs though, so each one needs to be tested so my computer can tell me what they correspond to. One is for the video and the other for the microphone. | |||
}} | |||
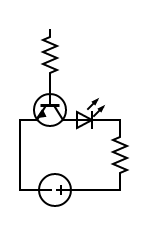
[[File:Circuit.png|thumb|right|A simple circuit to test for analog audio with 2 resistors, a transistor, and an LED. Connect the microphone to ground and the top resistor. If it's analog, the LED will flicker only when you talk. If it's digital, it won't light because USB is controller-initiated.]] | |||
One of the easiest hardware hacks is converting a harvested laptop webcam into a USB webcam. You can often get them for cheap or free from computer houses or bulk broken laptops. The trick here is that laptop webcams almost always use USB to connect, so it's a simple matter of identifying 4-5 pins on a connector, then soldering them to a USB connector. Some care must be taken because they sometimes use a nonstandard voltage like 3.3V for the power supply, so hooking them up without a voltage regulator can fry them. Usually they don't need logic-level converters because they still use standard 5V USB for the data. | |||
First, search for the camera module number. This is a popular hack so someone probably already did it. If you can't find anything, the cable that connects the webcam to the laptop may be properly colored. In these cases, Red means Vcc, Black (or bare) means GND, Green means D+ and White means D-. There are sometimes extra wires for stuff like the built-in microphones or the activity light. You should always try to verify just in case the colors are wrong. If they're labeled, you can usually trust that. | |||
Checking ground is easiest because you can test continuity to the large copper pads or RF shields. Sometimes ground has multiple pins. Vcc is trickier, but it's usually the furthest pin from ground and will have wires connecting to small three-pin components (voltage regulators). | |||
Microphones will have 2 wires, but what those are for depends. Analog mics have data and analog-ground. This is sometimes tied to digital-ground, but if it isn't then you'll want to try both orientations. Digital mics are USB devices themselves, and should be checked for D+ and D-. When testing, make absolutely sure you don't plug an analog microphone into a USB port, because they can have negative voltage which the USB port may not protect against. You can test this using the circuit to the right. | |||
D+ and D- are the hardest to check if they're unlabeled. Luckily, reversing them won't break anything, it just won't work. Connect them one way, and if it doesn't work, connect them the other way. As a sanity check, they should be covered in extra metal foil inside the cable going to the laptop. | |||
If you have a compatible laptop, you can also try using your multimeter to detect these voltages and signals. A multimeter still won't detect D+/D- though, because they both use positive voltages. | |||
=== | === LCD Driver === | ||
'''M.NT68676.2''' | |||
{{gallery | |||
|File:M-NT68676-2-HDMI-DVI-VGA-driver-board-Moniter-Kit-for-laptop-screen-LCD-LED-retrofit.jpg Q90.jpg | |||
| Image Credit: [https://www.aliexpress.us/item/2255801015618735.html AliExpress] | |||
|File:PXL 20230218 070337374.MP.jpg | |||
| My board with the UART adapter attached. | |||
}} | |||
This is a consumer-grade LCD driver for LVDS screen modules like you can harvest from broken laptops. Because the board itself is the product, almost no effort has gone into locking it down. However, it's also so straightforward that there aren't many things to actually poke at. | |||
The unpopulated header above the VGA on my board is labeled GND, TXD, RXD, 5V which is a bog-standard UART interface, but when I attached my UART adapter nothing came through even though it came with a header soldered on, suggesting it was used at the factory. It's possible there were multiple firmware versions, one which ran diagnostics and sent them to the header and another which disabled it. | |||
The main controller IC is a Novatek [https://datasheetspdf.com/datasheet/NT68667UFG.html NT68667UFG]. After finding its data sheet, we can see it has on-screen display support which you normally can't change, giving a good use-case for hacking. It also has an embedded 8031 microprocessor with external SPI memory, meaning even if we can't find an ISP we can still do whatever we want to the firmware with a programmer clip. | |||
To further investigate the dysfunctional header, I attached a continuity tester to the TXD/RXD pins, then dragged the other probe across the controller's pins until it beeped. According to the datasheet, those pins are for i2c and double as GPIO. To figure out what it's actually doing, the firmware would have to be decompiled and even then it might not even be there anymore. | |||
=== Portable DVD Player === | |||
'''Sony DVP-FX950''' | |||
{{gallery | |||
The | |File:610wiBrepRL._AC_SX679_.jpg | ||
| The original DVD player. Image Credit: [https://www.amazon.com/Sony-DVP-FX950-9-Inch-Portable-Player/dp/B003C2T1IU Amazon]. | |||
|File:PXL 20230218 212221319.jpg | |||
| The screen module. | |||
|File:PXL 20230218 212221319 2.jpg | |||
| The touch buttons and control board with bodge wires. | |||
|File:PXL 20230218 212249762.MP.jpg | |||
| The touch controller and video codec. | |||
}} | |||
Over 3 years ago, I bought a portable DVD player from Goodwill and scrapped it for parts. For various reasons, I just kept the screen, video controller, and buttons. It has a lot of interesting parts and is well labeled, making it very easy to hack. There are pads labeled Y_IN and C_IN, meaning it uses S-Video which is a very accessible analog video format we can output from a small computer. It also clearly labels SDA and SCL, which it uses to interface with the touch controller. On the touch controller itself there is a small 5-pin surface-mount header. But, it's not labeled so we need to do more research to see what it's there for. | |||
The | The touch controller is https://www.slideshare.net/alanlai.wae/ata2508-users-manual-v1 ATA2508]. Cross referencing the header with the datasheet, they are Vcc, (?, connected to main board), SDA, SCL, and GND. The unknown pin doesn't connect to the touch controller, but it does go to pin 4 of the flat cable to the main board, pin 44 of the video codec, and the touch pad labeled "R_T". | ||
When looking for the datasheet of the video codec, MST7915MC-LF, none exist. This is pretty common for obscure chips because manufacturers treat them as confidential for some reason. We can find a similar chip (same pin count and description) called [https://pdf1.alldatasheet.com/datasheet-pdf/view/1314845/ETC1/MST703.html MST703], but comparing the pins to ones we know for sure (eg the pin 1 Chip Select on the nearby flash chip) the pins seem to be shifted by 1. If that's the only difference, R_T may just be GPIOA and it could stand for "Transmit_Receive" suggesting a half-duplex debug line. At this point I would use the logic analyzer to see if it says anything, but mine broke. | |||
=== Monitor === | === Monitor === | ||
'''ViewSonic VX2235wm model VS11349''' | |||
{{Gallery | {{Gallery | ||
|File:PXL_20230218_032454175.jpg | |File:PXL_20230218_032454175.jpg | ||
| Cheap monitor from Goodwill I've had in my closet for | | Cheap monitor from Goodwill I've had in my closet for 2 years | ||
|File:PXL 20230218 033647553.jpg | |File:PXL 20230218 033647553.jpg | ||
| 9 screws and a spudger behind the bezel | | 9 screws and a spudger behind the bezel | ||
| Line 162: | Line 288: | ||
}} | }} | ||
This is a more advanced example. There are no headers or relevant test pads, and the underside has nothing at all. However, the two Realtek ICs are clearly labeled and easy to find confidential datasheets for. The one to the left is [https://pdf1.alldatasheet.com/datasheet-pdf/download/1314600/REALTEK/RTD2120S.html RTD2120S], an embedded 8061 microcontroller designed for monitors, and the one to the right is [https://datasheet-pdf.com/PDF/RTD2553V-Datasheet-Realtek-728324 RTD2553V], a TMDS/VGA decoder. This monitor must have been made before HDMI got big, because it has | This is a more advanced example. There are no headers or relevant test pads, and the underside has nothing at all. However, the two Realtek ICs are clearly labeled and easy to find confidential datasheets for. The one to the left is [https://pdf1.alldatasheet.com/datasheet-pdf/download/1314600/REALTEK/RTD2120S.html RTD2120S], an embedded 8061 microcontroller designed for monitors, and the one to the right is [https://datasheet-pdf.com/PDF/RTD2553V-Datasheet-Realtek-728324 RTD2553V], a TMDS/VGA decoder. This monitor must have been made before HDMI got big, because it has DVI-I instead of HDMI even though they have identical digital signals. Interestingly there's a much smaller chip in the upper left which is labeled ATMEL640, a very valuable find. | ||
Atmel is generally extremely hobbyist-friendly due to its AVR ATmega and ATtiny product lines which Arduino is built on, however documentation for this chip is unusually nonexistent. It may potentially be a knockoff chip (Atmel doesn't label its chips with ATMEL as part of the model number), but a little sleuthing looking for its package type (TSSOP-8, a thin 8-pin surface-mount IC) suggests it's related to ATtiny45, Atmel's pinouts don't have much variation, and a quick glance at what the pins connect with matches. 3 of the GPIOs are unused and tied to ground, while another 3 seem to match SPI and go to the RT2120S. Pin 1 should be the reset/debug pin, meaning this cannot be reprogrammed unless it already has a bootloader to allow programming over SPI. | |||
According to the datasheet of the RT2120S, it supports ISP (In-System Programming) via the DDC lines of ''both'' the DVI and VGA DDC buses (Display Data Channel, standardized i2c at addresses 0x50 and 0x51 which give information about the supported display resolutions). Thus, we know how they programmed it in the factory, how to download the firmware for, and how to upload custom firmware. There's also an enormous amount of room we could shove a tiny computer into if needed. It also has dozens of GPIO which probably connect to the RTD2553V's parallel bus to give it commands and draw simple graphics which we could customize. | |||
== Resources == | |||
== | === News === | ||
* [https://hackaday.com/ Hackaday] | * [https://hackaday.com/ Hackaday] | ||
== | === Youtube channels === | ||
* [https://www.youtube.com/channel/UCtM5z2gkrGRuWd0JQMx76qA bigclivedotcom] | |||
* [https://www.youtube.com/@greatscottlab GreatScott!] | |||
* [https://www.youtube.com/@ZackFreedman VoidStar Labs] | |||
* [https://www.youtube.com/@ExplainingComputers Explaining Computers] | |||
* [https://www.youtube.com/@ElectroBOOM ElectroBOOM] | |||
* [https://www.youtube.com/@EEVblog EEVblog] | |||
* [https://www.youtube.com/@element14presents Element14 Presents] | |||
* [https://www.youtube.com/@BenEater Ben Eater] | |||
* [https://www.youtube.com/@Computerphile Computerphile] | |||
* [https://www.youtube.com/@hackaday Hackaday] | |||
=== Lectures === | |||
* [https://www.youtube.com/watch?v=VY9SBPo1Oy8 Hacking Everything: Re-purposing Everyday Devices] | |||
* [https://www.youtube.com/watch?v=nruUuDalNR0 Extracting Firmware from Embedded Devices (SPI NOR Flash)] | |||
* [https://www.youtube.com/watch?v=01mw0oTHwxg Hacker's Guide to UART Root Shells] | |||
* [https://www.youtube.com/watch?v=HuCbr2588-w Intro to Hardware Hacking - DEF CON 27] | |||
* [https://www.youtube.com/watch?v=tlwXmNnXeSY Crash Course in How to be a Hardware Hacker] | |||
* [https://www.youtube.com/watch?v=-WeDzPGyFxs Hardware Hacking 101] | |||
* [https://www.youtube.com/watch?v=hWYzgw0WhYU A Hacker's Guide to Hardware Hacking] | |||
* [https://www.youtube.com/watch?v=qAxJBx8GiN0 DEF CON Safe Mode Hardware Hacking Village] | |||
=== Credits === | |||
* [http://www.batsocks.co.uk/readme/pdi_headers.htm Batsocks] | |||
* [https://partsbox.com/blog/choosing-a-debug-programming-connector-2019.html PartsBox] | |||
* [https://electronics.stackexchange.com/questions/437423/ what-are-these-round-pads-on-the-bottom-of-a-pcb StackExchange] | |||
* [https://www.amazon.com/Sony-DVP-FX950-9-Inch-Portable-Player/dp/B003C2T1IU Amazon] | |||
* [https://www.aliexpress.us/item/2255801015618735.html AliExpress] | |||
* [https://www.amazon.com/Sony-DVP-FX950-9-Inch-Portable-Player/dp/B003C2T1IU Amazon] | |||
Latest revision as of 01:45, 20 February 2023
Physical access is root access
— Security Operations
Hardware hacking means modifying existing electronics to use them in a way they were not intended to be used. Normally this means hacking in order to gain privilege escalation and compromise security, but it's equally applicable to unlocking the hidden capabilities of a DVD player to act as a file server for backups.
The complexity of a hack depends primarily on the intended market of the device. Usually the cheaper and simpler something is, the less they bothered to remove extra debug and programming hardware before sending it to market. Smartphones have an extreme level of complexity so they tend to be heavily locked down and require a lot of research, if it's even possible for a hobbyist. On the other hand, devices which don't have any significant level of miniaturization tend to still have everything the developers used to create the hardware in the first place.
Audience
This how-to is intended for anyone with a passing knowledge of circuitry, but not much else. If you know what "Arduino" is, this is probably for you. It can get slightly technical, but even absolute beginners should be able to follow along with Google open to look up anything they're not familiar with.
Scope
This article is specifically focused on techniques to start unlocking hardware capabilities. Soldering, using the tools, and firmware are all out of scope and will require additional research by the reader. The topic itself is already incredibly broad, so it doesn't make sense to talk about the specific techniques after initial hacking. Soldering is an art form in itself, one which requires a lot of practice to get good at, and firmware varies so wildly between chips that it would take a dozen more articles of this length to even give an overview. Above all else, this article is to introduce people to the basics of hardware hacking and to encourage more research to actually put these techniques to practice.
Terminology
- GND (Ground)
- A reference to 0 voltage which determines the voltage of the rest of the circuit.
- Vcc
- Nominal voltage of the circuit, usually 5V or 3.3V.
- Header
- Through-hole or surface-mount exposed copper pads which can have pins soldered into them for easy access
- Line/wire
- A data signal for a particular protocol.
- Bus
- One or more lines implementing a protocol.
- Half-duplex
- A bidirectional line where data is transmitted in exactly one direction at any given time.
- Full-duplex
- A two-wire bidirectional bus where each line transmits in only one direction, so data can be flowing in both directions simultaneously.
- Serial / Parallel
- A line which communicates one bit at a time, rather than a parallel line where eg 8 bits of a byte are sent across 8 wires simultaneously.
- Synchronous / Asynchronous
- A synchronous bus has a clock which synchronizes a line between a controller and peripheral.
- Active high / low
- The line is considered "on" or the 1 bit when the voltage is high/low. Active low sounds weird, but it's primarily used for alert signals because it can be implemented with a single transistor.
- Interrupt
- A line which alerts the controller that the peripheral has something to say.
- IC
- Integrated Circuit, small black squares with bits of metal (pins) on the sides which have all the hardware inside to perform a particular function. These include everything from voltage regulators to microcontrollers and external memory.
- PCB
- Printed Circuit Board
- Bodge wire
- A wire added to a circuit board by an end-user to connect things that weren't connected before.
Tools
When ordering tools, you can find them on Amazon and they'll arrive in days while they're 2-3 times cheaper on AliExpress but take a month to ship from China.
Disassembly
Most of these you probably already have or some equivalent. They're used to disassemble a device to expose them for hardware hacking.
- Screwdrivers
- Usually only phillips are needed of various sizes. A hex driver set is a valuable tool for taking anything apart.
- Spudger
- This is any thin, flat object which can be used to pry a tabbed case apart. Ideally this should be plastic or rubber because there's less chance of it damaging the casing or cutting your fingers when you slip.
- Superglue
- For when you inevitably break the case, superglue can help repair it.
Investigation
These tools are used for investigating a circuit when signals are mislabeled or not labeled at all. None are actually required, but they make life easier.
- Multimeter ($10 Amazon, $5 Ali)
- Voltmeters can identify power supplies, voltage levels, and active signals.
- Continuity testers help identify where wires are connected.
- Ohmeters determine resistances, which can be used in Ohm's Law calculations.
- Single-Board Computers with these interfaces exposed
- Raspberry Pi Zero ($10)
- Multi-interface adapters (if you can't get an SBC)
- FT232H USB to JTAG/UART/I2C/SPI Module ($18 on Amazon, $6 on AliExpress)
- CH341A USB to UART/I2C/SPI ($9 on Amazon, $4 on Ali)
- Logic Analyzer ($13 Amazon, $5 on Ali)
- These are not necessary, but can be invaluable for identifying unmarked headers.
- Oscilloscope ($30 Amazon, $25 on Ali)
- Useful for debugging faulty and analog signals. Good oscilloscopes run several hundred dollars, but functional versions can be found for $25.
Single-interface adapters (especially for UART and i2c) are available, but not much cheaper than the multi-interface adapters.
Soldering
Soldering is melting a low melting-point metal called "solder" to connect components to a circuit board. It's not always necessary in hacking, but can be incredibly useful to attach wires so they don't have to be held in place.
- Solder ($5)
- Soldering iron ($10)
- Solder flux ($5 Amazon, $2 Ali)
- Fume extractor/fan (varies)
- Not strictly necessary, you can solder in a well-ventilated area but even then these are a good idea to have because breathing in heavy metals isn't usually a good idea.
- Solder wick braid ($4 Amazon, $2 Ali)
- Used to remove excess solder and remove soldered components
- Heat gun ($12 Amazon, $5 Ali)
- Relatively rare you need to use one, mostly useful for adding or removing components with a lot of pins, or when there's massive heatsinks a soldering iron can't heat up fast enough.
Other
- SOIC8 programmer test clip ($8 on Amazon, $2 on Ali)
- Useful for more advanced hacking when you can find an external program memory, allowing you to read and write firmware without removing it.
How-to
Selection
When hardware hacking, the kind of device you try to hack is very important. You want cheap, old, low-effort devices ideally owned by millions of people. If you don't have one in mind, thrift stores are an excellent source of these. Always keep in mind the capabilities of the device; you will never be able to turn a DVD player into a high performance computer, but you might be able to embed other devices into it to make it a multimedia center.
Unfortunately many devices with high hack-potential are also incredibly tightly locked and not even professional hackers have managed to get them to do anything except their intended function. This includes most smart phones, which are just too tightly engineered to have easy access points, but also products like Amazon Alexa have been found to be near unhackable, as cool as it would be to install your own custom assistant firmware.
Google it
As fun as it can be to figure out how to hack a device, there's a good chance someone else has already figured it out and they probably did it better than you can. Google the model number before you even open it, because you might find someone else determined it to be too much trouble to hack and you can save the effort.
Open the case
Before anything, unplug the device and maybe even let it rest 30 minutes.
Great care must be taken when opening any device, especially new ones, because the case may have hidden tabs you can accidentally break off or glue which requires enough force to break the case. It's usually possible to open a device without any damage or force. Look for screws, which may be under stickers or rubber feet, and stick flat objects into any grooves you see. Apply some force to see if it will give, but if you have to use too much you probably missed a fastener somewhere.
At each step of the disassembly, take a picture of what it looked like so you know what it should look like after you put it back together. Take note of the size and shape of each screw as well, as they may differ and require some kind of organization to match them back to their original place. You don't have to be so thorough as to match each screw to exactly where it came from, just which sizes go with which locations.
Disassembly
Once the case is open, you'll see the guts of the device itself. This is the easy part of disassembly because at this point it's designed for serviceability. Keep taking pictures and unscrew every circuit board or component you can find until everything is in pieces. This lets you see all sides of the boards, any markings they might have, and any headers they might be hiding. Often devices will contain multiple boards connected by board-to-board cables like flat cables or JST connectors. You need to unplug them as needed, also taking note of how and where they connect to each other.
If you see a thick board with a lot of black tubes on it, this is probably the power supply unit and you should be very careful when handling it. They aren't dangerous on their own, but those big black tubes are called "capacitors". They're discrete components which store charge like batteries, but are optimized to release all their energy at once. Unscrew the PSU, then take your screw driver and touch the metal bits underneath the black tubes to discharge them. If they're thumb-sized or bigger, they may make a loud POP, and afterwards do nothing. Unless they're in a CRT TV they're probably not lethal, but it will hurt a lot if you touch them before discharging. Most products made after the 1990s will only have these massive capacitors on the PSU, and if they do have them on other boards they're probably there for their high capacitance (to eg filter audio signals) rather than their charge capacity.
Header Hunting
The first things you should look for are headers. These stand out a lot. They're lots of big holes close together and covered in metal. Usually during development, these have header pins soldered into them so the developers can easily plug in their test equipment. Then when they go to market, they aren't removed because doing so would mess up circuit routing, require they be added back in if further revisions are done, and then there'd be no way to test hardware faults reported by customers. Because they're used for testing and development, they tend to give a lot of access to the hardware for little to no effort, though sometimes ICs are programmed to disable their debug capabilities. Rarely they'll even still have pins in them (to make flashing the firmware at the factory easier).

Once found, look for silkscreen text nearby which labels the pins. There's a lot of variation in the labels, but generally it should make at least some sense. Any which are labeled ICP, ISP, ICSP, PDI, Debug, Comm, Port, etc are probably going to be very useful.
Test Pads

If no interesting headers can be found, you can also look for test pads. These are moderately-sized (around 1 mm) circles or squares of (possibly tinned) exposed copper which give easy access to a line. In generous designs, they'll even be labeled, but this is less common than for headers.
If the test pads aren't labeled, it's time to do research and use your continuity tester to cross-reference with IC datasheets. This can be tedious but rewarding for what it can uncover. Often, test pads expose unused pins on an IC, which can be incredibly useful for custom firmware.
Research
More often than not, headers and test pads either don't exist or aren't properly labeled. When this happens, it's time to Google the IC part numbers. This is probably the most frustrating step, as manufacturers treat their datasheets as confidential. They like to hide them behind inquiry forms, and you can bet your inquiry is going straight into the trash if you're ordering less than 1000 units, much less inquiring about a unit they've already sold. Luckily they don't seem to be especially litigious for sites which host datasheets very clearly watermarked as confidential, so they still tend to get out.
First, try googling just the part number. It might not be confidential, or it might be consumer-grade so they actually want you to see it. It might be on the manufacturer's website, a distributor, a datasheet aggregator, or just a raw PDF. It's always nice when this is all you need to find it.
Otherwise, you can try searching "<part number> datasheet" or even "<part number> datasheet ext:pdf". Sometimes even this isn't enough, and you have to branch out. You can try searching for "<part number> pinout"; it's not ideal, since you won't know exactly how the chip works, but a pinout can at least give you an idea of what's going on. Occasionally I've found pinout images or EDA footprints created by hobbyists who found it somehow. Datasheet aggregators like alldatasheet.com list ICs with similar part numbers and their descriptions, and oftentimes manufacturers won't significantly change the pinouts between versions. When using this information, you should always double check to avoid frying a chip.
In the worst case scenario where no information about a chip can be found, pinouts may need to be reverse-engineered. Power pins are the easiest because they can be found with multimeters and visual clues like the width of the wire. Ground will always be made of big blobs of copper that fill unused areas, while Vcc tends to have slightly larger wires. Circuits almost always have more than one chip, so if information can be found on them they can be cross-referenced along with labeled test pads and connectors. Buses tend to be routed together, so through visual inspection groups of 2-5 wires can be identified and connected to a logic analyzer. If there are no test pads on these and you're really desperate, you can carefully scrape off the solder mask to expose the bare copper underneath. If you accidentally cut the wire, you can solder a bodge wire on top without much issues.
The easiest way to match other pins, headers, and pads to an IC's pins is to put one of the continuity tester's probes on the known signal, and drag the other probe across each row of pins until it beeps. This gives you a general idea of where it's connected which can be narrowed down until the exact pin is found.
Sometimes you'll find an 8-pin EEPROM memory chip nearby. These are great because they usually store firmware or configuration data. Then if you can't find datasheets, you can still dump the firmware, detect what architecture it's using, and convert it to human-readable code it to see what it's doing.

Don't be afraid to give up on a chip, either. If no information can be found, it's not really worth reverse-engineering because even if you reverse engineer everything you probably won't be able to hack it. In cheaper products, there are even what are called "glob-tops" which are bare silicon dies coated in black epoxy which are never labeled.
Hacked
Once you have a decent understanding of the circuit and how it functions, you should have a good idea of how it can be changed and what to do to change it, or at the very least a lead on how to research it. The easiest hacks are those that require only a simple rewiring, or replacing switches with relays to automatically push buttons etc. The most rewarding hacks will involve rewriting firmware or embedding an extra microcontroller (with its own firmware) to control peripherals as needed.
Sometimes you'll find a circuit can't really be hacked with your skill level, or what's available isn't that interesting. For these cases, it's best to cut your losses and either give it back to Goodwill or strip it for parts to use in other projects. Connectors, buttons, switches, LEDs, batteries, and even some daughterboards like the PSU are all useful. Occasionally they'll have a well-documented IC which is worth harvesting as well. Don't bother harvesting discrete components like resistors, capacitors, or inductors unless you're severely strapped for cash, they cost less than $5 for packs of 500.
Silkscreen
Most PCBs have what's called a "silkscreen", which is white or black ink drawn on the board to aid manufacturing and keep track of which components go where. Most of these will be "reference designators", an alphabetic prefix with a numerical suffix. This isn't super useful, but can aid in identifying what signals various wires carry. Some common reference designators include:
- R - Resistor, restricts the flow of voltage
- C - Capacitor, stores charge to suppress voltage ripples and filter signal frequencies
- L - Inductor, resists high frequencies
- D - Diode, only lets current flow in one direction
- Q - Transistor, a kind of electronic switch
- U - Integrated Circuit
- F - Fuse, literally breaks if too much current flows through it to protect from power surges
- H - Hardware eg screws
- J - Jack, some kind of connector to carry signals into or off of a PCB
- JP - Jumper, exposed copper pads close together which lets you connect two lines together, usually to set some semi-permanent configuration by the manufacturer
- S - Switch or button
- T - Transformer, usually used in power supplies to convert AC to DC
- TP - Test Point, exposed copper pads which give easy access to a signal line or power wires
- X(TAL) - Crystal oscillator
- H - Pin Header
There are hundreds more, and they aren't always what they normally mean. Reference designators are not a standard, they're maintained by convention alone.
The ones you want to pay the most attention to are U, H, J, and JP (IC, Header, Jack, and Jumper) although it's also usually obvious what they are just by looking at them.
Interfaces
There are 5 interfaces which you'll find most often in hardware hacking: RS-232 (aka UART), SPI, i2c, JTAG, and SWD. More recognizable interfaces like USB are primarily used for inter-device communication, though embedded USB does exist. There are other more exotic interfaces like 1-wire, UNIO/O, CAN, i2s, CEC, and a veritable zoo of debug interfaces, but they aren't very common or useful for hacking.
RS-232
RS-232 (Recommended Standard 232) is an extremely old serial protocol from 1960 used for teletypewriter operator consoles and more rarely inter-chip communication. Nowadays it's more commonly referred to as U(S)ART (Universal Synchronous/Asynchronous Receiver/Transmitter) which is technically a physical implementation used for communication standards such as RS-232. Because UART isn't a communication standard per-se, it has a lot of variation in its interface.
At its most extreme, a UART-based interface can be a single wire half-duplex interface, where the peripheral and controller both have control over the bus and have to agree ahead of time which one should control the bus at any given time to avoid thrashing communication.
Usually a chip's UART will use two wires (Tx and Rx) to implement a full-duplex stripped down RS-232. UART is almost always signaled with 0V for bit 0 and 3.3V for bit 1. Sometimes there is also frame bits to let devices know when communication starts, checksum bits to detect transmission errors, or exotic word sizes, all things which should be checked for if the defaults don't work. Baud rate (the frequency the bits are transferred) will also probably need adjusting because there's a lot of variation. 9600 and 115200 are the most common I've seen (in bits per second).
More rarely a chip will implement more RS-232 signals which you can connect to most USB adapters. They're almost never necessary because they communicate readiness to receive data, and even the cheapest microcontrollers are fast enough to always be available. If you ever need them, it's good to know that RS-232 calls the terminal that connects to a device "DTE" (Data Terminal Equipment) and the device itself "DCE" (Data Communications Equipment). This was from the dawn of computers when you had one big shared mainframe and dozens of "dumb terminals" which let you run commands and see their results.
SPI

SPI (Serial Peripheral Interface) is an old (1980s) communication protocol nowadays primarily used for EEPROM memory, which can be useful for hacking budget microcontrollers that don't have their memory integrated. Communication is toggled by enabling the Chip Select (CS) line.
In 2022, the OSHWA (Open Source HardWare Association) changed the acronyms used by SPI because of their tacit usage of slavery terminology. For at least a few more years one is likely to see both kinds in the wild, so both are listed here.
- MISO / POCI - Master In Slave Out / Peripheral Out Controller In
- MOSI / PICO - Master Out Slave In / Peripheral In Controller Out
- SS / CS - Slave Select / Chip Select, active-low enabling a chip to listen. Sometimes omitted if only one device is on the bus
- SDI / SDO - Serial Data In / Serial Data Out, can be either POCI or PICO depending on if the device is a controller or peripheral
- INT - Interrupt, relatively rare for SPI
SPI can be half-duplex using only one wire (plus Chip Select), but this is very rare. Communication is initiated by the controller, then it stays quiet while it waits for the peripheral's response which has some method of saying when it's done.
Variations exist for transmitting 2 (Dual SPI), 4 (Quad SPI or QSPI), and even 8 (OctoSPI) bits at a time. QSPI is actually used by most modern SD cards. For low-level hacking, only Single SPI is actually useful because the others are meant for high-bandwidth memory rather than eg program memory.
i2c
i2c (Inter-Integrated Chip) is an old (1980s) communication protocol which is used nowadays for peripheral control. Unlike SPI, it's packetized and toggled by 7 or 10 bit addresses. It's very useful for controlling peripherals directly when you can't get access to the microcontrollers.
- SDA - Serial DAta
- SCL - Serial CLock
- INT - INTerrupt, very common for i2c
JTAG
JTAG (Joint Test Action Group) is an old (1980s) synchronous factory test standard allowing boundary scanning and ICSP of daisy-chained chips. It uses no less than 5 signals, and often many more, but is very powerful if you can find it because it usually gives you complete and total access to every JTAG-enabled chip on the board.
- TDI - Test Data In
- TDO - Test Data Out
- TCK - Test ClocK
- TMS - Test Mode Select
- TRST - Test ReSeT (optional)
SWD
SWD (Serial Wire Debug) is a very new (2017) 2-wire variant of JTAG defined used by low pin count ICs. Unlike JTAG, it does not support daisy chaining and so the access it provides is limited to a single IC and interfaces which can be explicitly accessed via the JTAG registers. If you find an unlocked SWD interface, you're done. It gives you complete control over the system with only 2 wires, and is powerful enough to let you read and write registers and memory of the microcontroller while it's running.
- SWDIO - Serial Wire Data Input/Output
- SWCLK - Serial Wire CLocK
Examples
Laptop Webcam
One of the easiest hardware hacks is converting a harvested laptop webcam into a USB webcam. You can often get them for cheap or free from computer houses or bulk broken laptops. The trick here is that laptop webcams almost always use USB to connect, so it's a simple matter of identifying 4-5 pins on a connector, then soldering them to a USB connector. Some care must be taken because they sometimes use a nonstandard voltage like 3.3V for the power supply, so hooking them up without a voltage regulator can fry them. Usually they don't need logic-level converters because they still use standard 5V USB for the data.
First, search for the camera module number. This is a popular hack so someone probably already did it. If you can't find anything, the cable that connects the webcam to the laptop may be properly colored. In these cases, Red means Vcc, Black (or bare) means GND, Green means D+ and White means D-. There are sometimes extra wires for stuff like the built-in microphones or the activity light. You should always try to verify just in case the colors are wrong. If they're labeled, you can usually trust that.
Checking ground is easiest because you can test continuity to the large copper pads or RF shields. Sometimes ground has multiple pins. Vcc is trickier, but it's usually the furthest pin from ground and will have wires connecting to small three-pin components (voltage regulators).
Microphones will have 2 wires, but what those are for depends. Analog mics have data and analog-ground. This is sometimes tied to digital-ground, but if it isn't then you'll want to try both orientations. Digital mics are USB devices themselves, and should be checked for D+ and D-. When testing, make absolutely sure you don't plug an analog microphone into a USB port, because they can have negative voltage which the USB port may not protect against. You can test this using the circuit to the right.
D+ and D- are the hardest to check if they're unlabeled. Luckily, reversing them won't break anything, it just won't work. Connect them one way, and if it doesn't work, connect them the other way. As a sanity check, they should be covered in extra metal foil inside the cable going to the laptop.
If you have a compatible laptop, you can also try using your multimeter to detect these voltages and signals. A multimeter still won't detect D+/D- though, because they both use positive voltages.
LCD Driver
M.NT68676.2
-
Image Credit: AliExpress
-
My board with the UART adapter attached.
This is a consumer-grade LCD driver for LVDS screen modules like you can harvest from broken laptops. Because the board itself is the product, almost no effort has gone into locking it down. However, it's also so straightforward that there aren't many things to actually poke at.
The unpopulated header above the VGA on my board is labeled GND, TXD, RXD, 5V which is a bog-standard UART interface, but when I attached my UART adapter nothing came through even though it came with a header soldered on, suggesting it was used at the factory. It's possible there were multiple firmware versions, one which ran diagnostics and sent them to the header and another which disabled it.
The main controller IC is a Novatek NT68667UFG. After finding its data sheet, we can see it has on-screen display support which you normally can't change, giving a good use-case for hacking. It also has an embedded 8031 microprocessor with external SPI memory, meaning even if we can't find an ISP we can still do whatever we want to the firmware with a programmer clip.
To further investigate the dysfunctional header, I attached a continuity tester to the TXD/RXD pins, then dragged the other probe across the controller's pins until it beeped. According to the datasheet, those pins are for i2c and double as GPIO. To figure out what it's actually doing, the firmware would have to be decompiled and even then it might not even be there anymore.
Portable DVD Player
Sony DVP-FX950
-
The original DVD player. Image Credit: Amazon.
-
The screen module.
-
The touch buttons and control board with bodge wires.
-
The touch controller and video codec.
Over 3 years ago, I bought a portable DVD player from Goodwill and scrapped it for parts. For various reasons, I just kept the screen, video controller, and buttons. It has a lot of interesting parts and is well labeled, making it very easy to hack. There are pads labeled Y_IN and C_IN, meaning it uses S-Video which is a very accessible analog video format we can output from a small computer. It also clearly labels SDA and SCL, which it uses to interface with the touch controller. On the touch controller itself there is a small 5-pin surface-mount header. But, it's not labeled so we need to do more research to see what it's there for.
The touch controller is https://www.slideshare.net/alanlai.wae/ata2508-users-manual-v1 ATA2508]. Cross referencing the header with the datasheet, they are Vcc, (?, connected to main board), SDA, SCL, and GND. The unknown pin doesn't connect to the touch controller, but it does go to pin 4 of the flat cable to the main board, pin 44 of the video codec, and the touch pad labeled "R_T".
When looking for the datasheet of the video codec, MST7915MC-LF, none exist. This is pretty common for obscure chips because manufacturers treat them as confidential for some reason. We can find a similar chip (same pin count and description) called MST703, but comparing the pins to ones we know for sure (eg the pin 1 Chip Select on the nearby flash chip) the pins seem to be shifted by 1. If that's the only difference, R_T may just be GPIOA and it could stand for "Transmit_Receive" suggesting a half-duplex debug line. At this point I would use the logic analyzer to see if it says anything, but mine broke.
Monitor
ViewSonic VX2235wm model VS11349
This is a more advanced example. There are no headers or relevant test pads, and the underside has nothing at all. However, the two Realtek ICs are clearly labeled and easy to find confidential datasheets for. The one to the left is RTD2120S, an embedded 8061 microcontroller designed for monitors, and the one to the right is RTD2553V, a TMDS/VGA decoder. This monitor must have been made before HDMI got big, because it has DVI-I instead of HDMI even though they have identical digital signals. Interestingly there's a much smaller chip in the upper left which is labeled ATMEL640, a very valuable find.
Atmel is generally extremely hobbyist-friendly due to its AVR ATmega and ATtiny product lines which Arduino is built on, however documentation for this chip is unusually nonexistent. It may potentially be a knockoff chip (Atmel doesn't label its chips with ATMEL as part of the model number), but a little sleuthing looking for its package type (TSSOP-8, a thin 8-pin surface-mount IC) suggests it's related to ATtiny45, Atmel's pinouts don't have much variation, and a quick glance at what the pins connect with matches. 3 of the GPIOs are unused and tied to ground, while another 3 seem to match SPI and go to the RT2120S. Pin 1 should be the reset/debug pin, meaning this cannot be reprogrammed unless it already has a bootloader to allow programming over SPI.
According to the datasheet of the RT2120S, it supports ISP (In-System Programming) via the DDC lines of both the DVI and VGA DDC buses (Display Data Channel, standardized i2c at addresses 0x50 and 0x51 which give information about the supported display resolutions). Thus, we know how they programmed it in the factory, how to download the firmware for, and how to upload custom firmware. There's also an enormous amount of room we could shove a tiny computer into if needed. It also has dozens of GPIO which probably connect to the RTD2553V's parallel bus to give it commands and draw simple graphics which we could customize.
Resources
News
Youtube channels
- bigclivedotcom
- GreatScott!
- VoidStar Labs
- Explaining Computers
- ElectroBOOM
- EEVblog
- Element14 Presents
- Ben Eater
- Computerphile
- Hackaday
Lectures
- Hacking Everything: Re-purposing Everyday Devices
- Extracting Firmware from Embedded Devices (SPI NOR Flash)
- Hacker's Guide to UART Root Shells
- Intro to Hardware Hacking - DEF CON 27
- Crash Course in How to be a Hardware Hacker
- Hardware Hacking 101
- A Hacker's Guide to Hardware Hacking
- DEF CON Safe Mode Hardware Hacking Village










